What is Nmap & How to use Nmap?
- Rohith
- Aug 5, 2021
- 7 min read
Updated: Sep 15, 2021
Nmap (network mapper) is a free open source tool created by "Gordon Lyon". Nmap can be used to do passive and active port scanning, endpoint detection, service detection, version detection, and operating system detection. It is used for network discovery and security audits.
Nmap is a powerful tool with lots of features it can also be used to FIREWALL/IDS EVASION AND IP SPOOFING.
How to download Nmap?
Open any browser of your choice and navigate to https://nmap.org/.
Now from there go to the Downloads tabs.
From there you can download it based on the operating system you use.
Note: Different operating system has different installation methods so check the installation manual to download Nmap on your respective operating system.
Which operating system can be used to download and run Nmap?
You can use any operating system to download and run Nmap some of them include,
Linux (all distributions)
Microsoft Windows
Mac OS X
FreeBSD, OpenBSD, and NetBSD
Sun Solaris
Amiga, HP-UX, and also Other Platforms
Note: If you are practicing hacking or doing it in a legitimate way(white hat hackers) then Kali Linux operating system is one of the best security OS with many prebuild tools in it that also includes Nmap you can also use the parrot operating system for the same purpose.
Where can I practice Nmap?
You can use Nmap on websites and systems to which you have permission to do so. If not you can use Metasploitable in a virtual box and use Nmap locally. We can also use the CTF platforms available like Hack The Box.
The easiest way to practice Nmap for people who are starting with it would be navigating to http://scanme.nmap.org/, which is a service provided by the Nmap Security Scanner Project and Insecure.Org for people to practice, to test and make sure that their Nmap installation is working properly.
Note: While using http://scanme.nmap.org/ make sure you restrict yourselves and not spam or brute force the server with requests.
How to use Nmap?
Nmap has many options to work with, so it's not possible to know all commands at all times. To get an in-depth documentation manual any time we can use,
nmap -h or nmap --help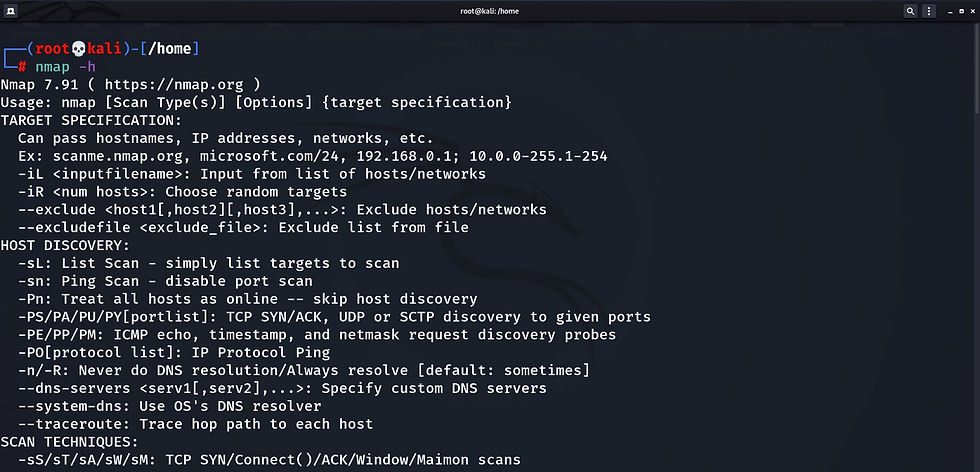
Ports defining:
The -p option in Nmap is used to specify the port number to be scanned,
nmap -p 80,443 // To scan the specified ports (80, 443).
nmap -p- or nmap -p1-65535 // To scan all the ports.
nmap --top-ports 10 // To scan the top 10 ports.
nmap -p U:53,137,T:21-25,80,139,8080 // To scan specified UDP (U) and TCP ports (T).Nmap Options:
Host Discovery:
This scan is similar to the basic ping request and is used for host discovery. It sends ICMP echo requests to find the availability of the host.
nmap -Sn 127.0.0.1This helps in identifying the active IP addresses. It can be valuable and very useful for network administrators when testing multiple IPs and checking whether they are active or not.
By default, Nmap does host discovery and then start performing port scan based on the given options, but we can also skip host scanning and directly deal with port scanning for any specified IP address by using,
nmap -p 22,80,443 -Pn 127.0.0.1 Now as we use the -Pn option we have disabled the host discovery and no ICMP echo request will be sent.
Scan techniques:
There are various scan techniques that can be used some of them includes,
-sS => TCP SYN scan:
Nmap sends SYN packets to the host but does not establish a connection or session hence there won't be any log generated at the host machine as no session is created. For this reason, an SYN scan is also called a stealth scan.
-sT => Connect scan:
The connect scan works only for TCP connections and it is not stealthy. In this case, Nmap connects and closes the connection without sending any data due to this reason it can be easily identified. So when a security analyst or system administrator sees multiple connect and close sessions without sending any data in the logs then it would be clear that someone has performed the connect scan on their system.
-sA => ACK scan:
It sends probes with an ACK flag set. When scanning unfiltered systems both open and closed ports return an RST packet. In this method, we cannot find whether the port is open or closed because both of them are reachable according to Nmap. Ports that do not respond or send ICMP error messages back are labeled as filtered.
-sI => Idle scan:
This is an advance scan where the IP address used to send packets to the host system would be another system within the host network.
eg,
nmap -sT -sU -p U:53,111,137,T:21-25,80,139,8080 127.0.0.1
Here, -p is used to specify the ports.
U: and "T:" are used to define UDP and TCP ports respectively.
-sU is used to instruct Nmap to scan the UDP ports (TCP ports are scanned by default).
-sT is used to instruct Nmap to use connect scan technique.
Some firewalls and packet filtering routers will prevent from making an inbound TCP connection while allowing the outbound TCP connection in that case the above scanning techniques will not work as they will be blocked by the firewall or packet filtering routers.
So we use the NULL, FIN, and Xmass scanning techniques in this case. These techniques can penetrate through the firewalls as they clear the SYN bit. They are also stealthier when compared to the SYN scan.
-sN => TCP Null scan:
The TCP flag header is null in this case. It does not set any bits.
-sF => FIN scan:
In FIN scan, only the TCP FIN bit is set.
-sX => Xmas scan:
In this case, the FIN, PSH, and URG flags are set.
Nmap interprets the Null, FIN, and Xmas scan responses as follows,
Probe response Assigned state
No response = open | filtered
TCP RST packet = closed
ICMP unreachable = filtered
Version identification scanning:
To find the version info of the services that are running we use,
nmap -p 22 -sT 127.0.0.1 -sVHere, -p option is used to specify the port in this case 22 (SSH),
-sT is used for TCP connect scan,
-sU is used for scanning UDP ports and
-sV is used to find the version info of the services that are running.

The -sV option can be very useful when we do pentesting to find whether updated versions of the services are used or else if an old vulnerable service is used then it can be exploited with the help of CVE, Metasploit, exploit database, etc.
Operating System identification scanning:
At times knowing the operating system that is running on the victim's machine will be useful for further reconnaissance and to identify specific vulnerabilities.
For this, we use the -O option which helps in detecting the OS.
nmap -p- -sS 127.0.0.1 -OHere, -O => Option is used to detect the operating system of the host machine,
-p- => Is used to scan the entire port range (1-65535) and
-sS => Is used for TCP syn scan.
Note: The Nmap OS detection scan works great but it does not mean it will always return a result or the result returned will be 100% correct.
eg,
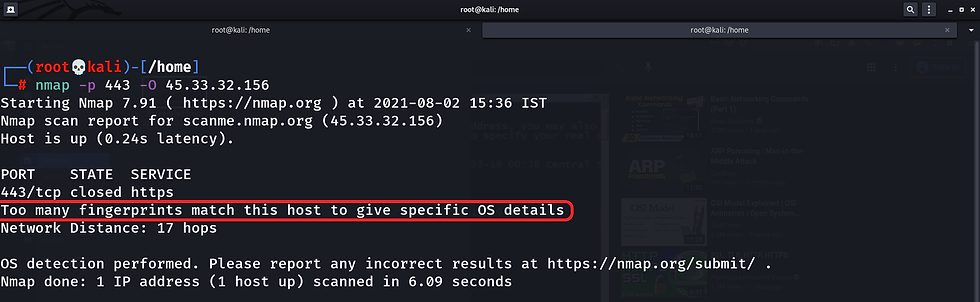
In case if you get a similar result try performing the "-A" option because during an aggressive scan we may get the result. We can also check the image below where we were able to find the OS for the same host using aggressive scan (-A).
Set Time:
When scanning multiple IP addresses and multiple or all ports it may take a very long time to complete the whole scan and in that case, we can boost the speed up by using the -T option.
We can use the -T option and give it a value range from 0-5 where 1 is the slowest and 5 being the fastest.
nmap -p 22,80,443,3306 -sT 127.0.0.1 -T 4Here, -T 4 is the timing template.

In the above image, we have used the same port numbers with the same TCP connect scan technique with the same IP but with 2 different -T options, and results are,
In the first case, we use -T 4, and the time taken to scan is 0.73 seconds.
And in the second case, we use -T 1, and the time taken to scan is 75.67 seconds
So from the above image, it is clear that there is a lot of difference in the speed when we change the -T value.
Note: We don't want to use higher T values every time because in some cases the server may block us due to rate limits or based on firewalls rules. At times like that, we can use the lower T values.
Set Verbose:
We can set verbose to get the live details of the scan. The verbose mode is set using -v.
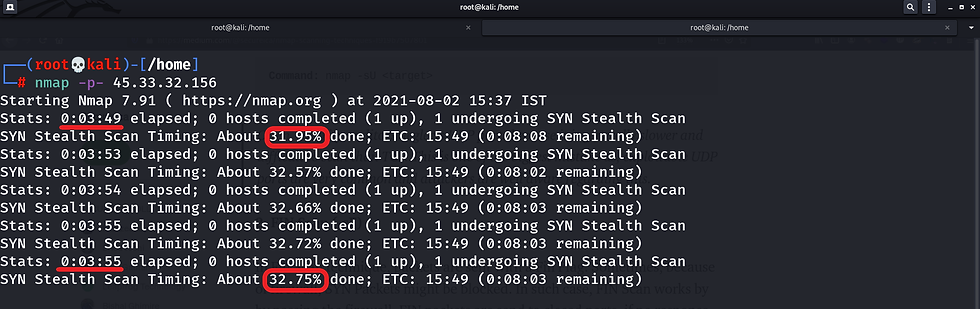
nmap -p- -sT 127.0.0.1 -T 4 -v Here, -v is used for verbose. we can also use -vv or more for greater effect.
nmap -p- -sT 127.0.0.1 -T 4 -vv We can also press enter key at any point in time to know the status of the scan.
Set Debugging:
When we don't get enough information from the verbose mode then we can use the debugging mode using the -d option.
nmap -p- -sT 127.0.0.1 -T 4 -d -d: Increases the debugging level, we can also use -dd or more for greater effect.
nmap -p- -sT 127.0.0.1 -T 4 -ddSet Output:
Now we have scanned the target so how do we Output the results in the desired format of our choice?
For that Nmap gives us some options they are,
-oN => outputs scan in normal form (txt).
-oX => outputs scan in XML form.
-oG => outputs scan in greppable form.
We can also use -oA option which saves the scan results in 3 different forms with extensions .nmap, .XML and, .gnmap.
nmap --open --top-ports 10 -oA 127.0.0.1 -T 4
Here, --open => Is used to show only open ports,
--top-ports 10 => Is used to scan the top 10 most common ports,
-oN => Is used to save the scan results in .txt format and
-T => Is used to give the timing for the scan.
And from the above image, we can see that the nmap.txt is the file name where the scan results have been saved. We can check it using the "ls" cmd to list the files in the current folder and view it using the "cat" cmd (cat nmap.txt). We can also use any text editor of our choice (vim, nano, etc) to edit the content of the nmap.txt file.
Misc:
In Nmap, if we want to get the entire details of the host in the scan result then instead of specifying separate options for each type of scan we can use the -A option.
The -A option enables OS detection, version detection, script scanning, and traceroute.
nmap -p 80,443 -A 127.0.0.1
Nmap -A is an aggressive scan. This option can be very useful for the system, network administrators, and also for automation purposes.
That's it guys cheers!! you have made it to the end of this awesome blog and you are ready to kickstart with Nmap before anything else, Nmap is a tool with several options it all depends on how you want to make use of it. Customize it according to your needs. Explore the tool and until next time stay freaky!!
Comment your favorite options or the Nmap command that you most frequently use and why do you think it is the best. Also do check our other posts on cyber and AI here.
Follow us on Instagram for the latest updates in Cybersecurity and AI.


Comments